Advanced Servers
The servers view of the services menu displays scaffolds that allow the operator to customize the behavior of various services integrated into the rXg.
Remote Database Access
The local database of an rXg may be configured for read-only access by third-party software tools When an rXg is configured with local server database storage. The local server database storage methodology configures the rXg to utilize PostgreSQL as the on board database. PostgreSQL is an advanced open source relational database with a wide variety of access options supported by both community-based open source projects as well as proprietary commercial offerings. A quick search for PostgreSQL GUIreveals numerous possibilities.
Many of the tools that integrate with PostgreSQL have GUIs for exploration. In addition, the vast majority allow for arbitrary execution of SQL queries.
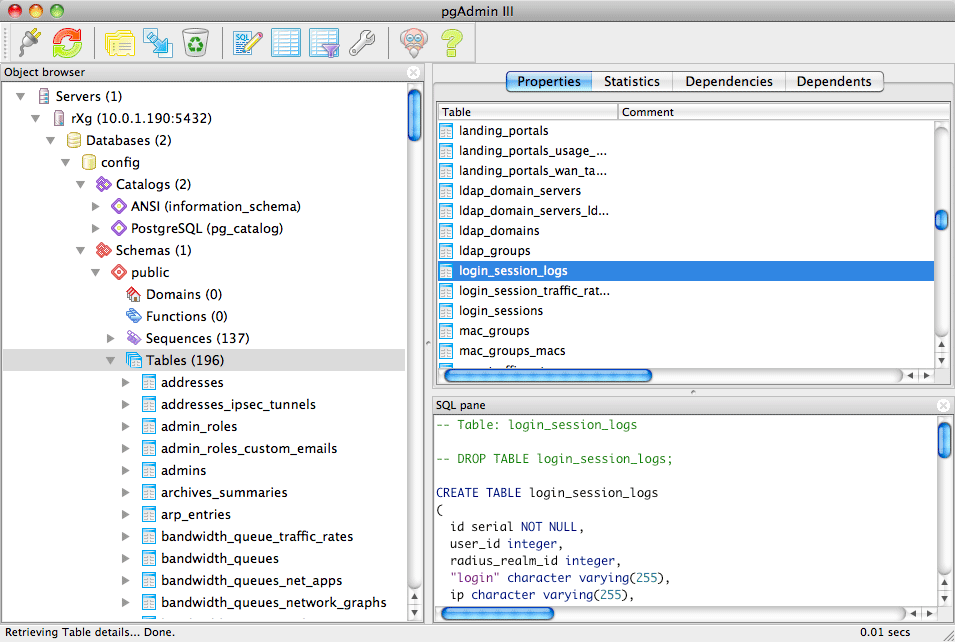
Remote access to the on board rXg database is used to accomplish a broad spectrum of tasks. Advanced and highly customized reporting is one common use case. Below is an example of a report generated by the pgAdmin PostgreSQL GUI tool for the login log.
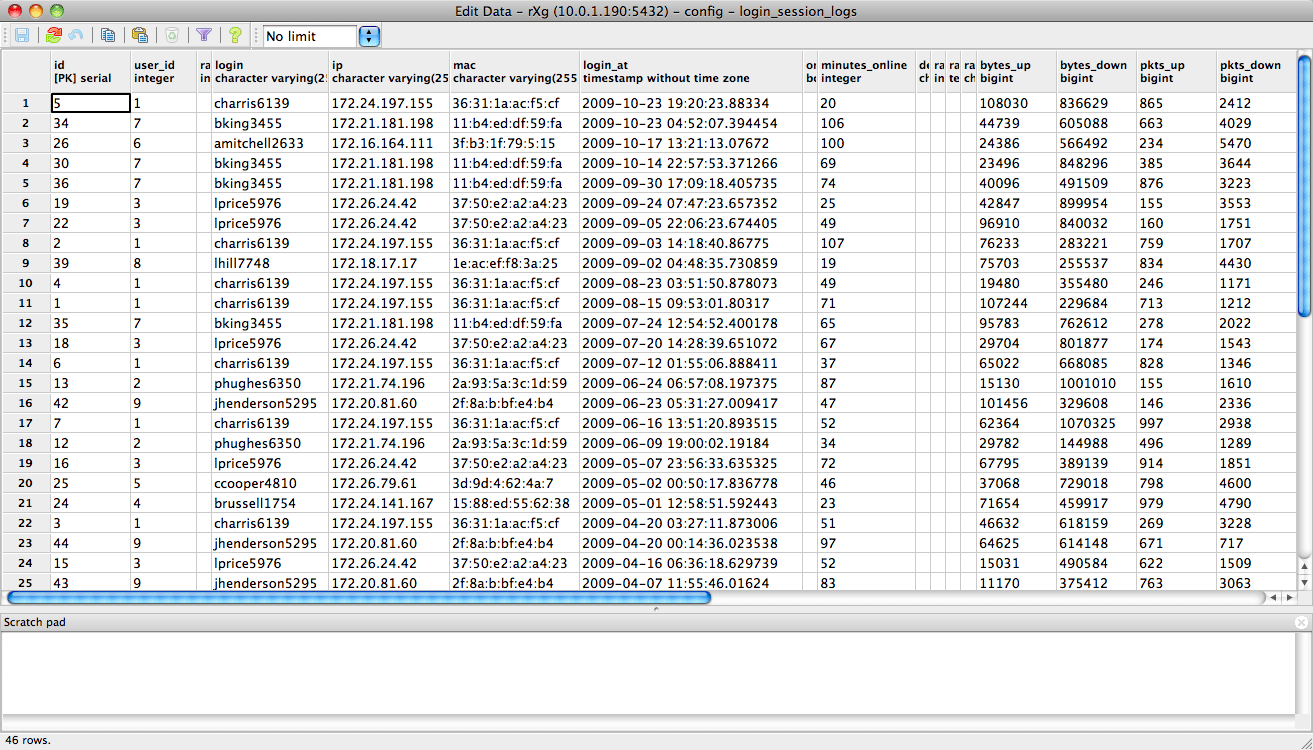
Another common use for remote database access is for integration with a third-party accounting system. Below is a report generated by pgAdmin from the credit card transactions log. A third-party accounting package could be configured to retrieve all of the transactions recorded in a particular time for automatic posting and reconciliation.
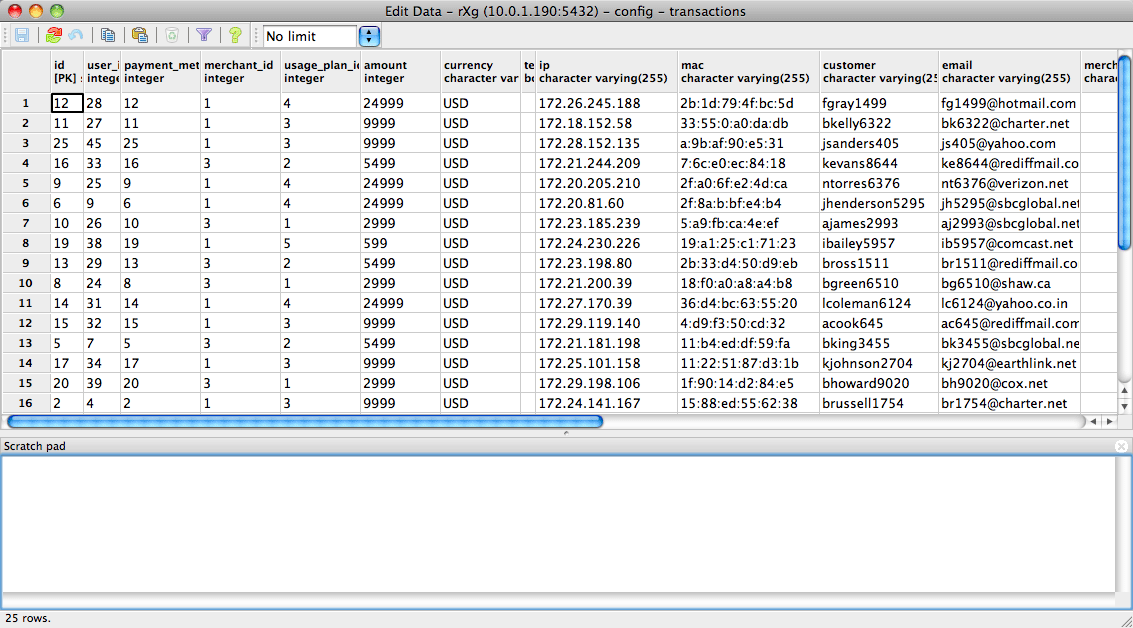
The remote database access feature is also a very convenient way to take periodic backups of the rXg database. This may be accomplished via GUI tools, but is also very easy to script. For example, thepg_dump utility may be run as a scheduled task on Windows or a cron job on a UNIX-based system to automate periodic backups of the rXg.
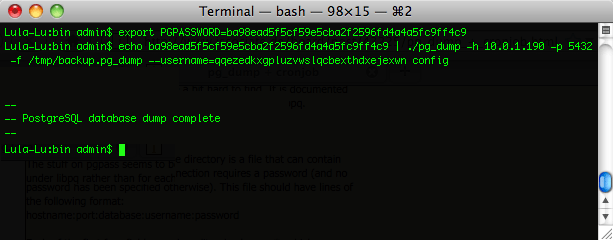
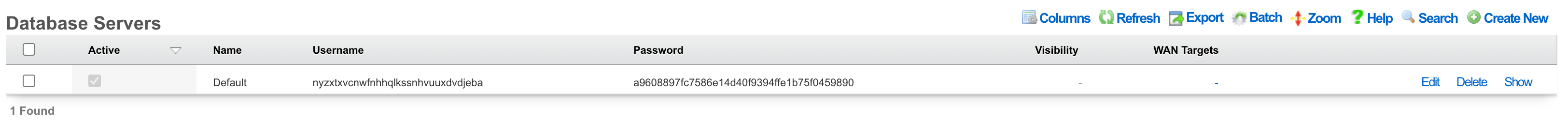
Remote database access is governed by the Database scaffold as discussed below. The default PostgreSQL port is used and the default database name is config. The name of the database being used by the rXg may be changed via the Cluster view of the administrative console. It is strongly advised that the default database name be used.
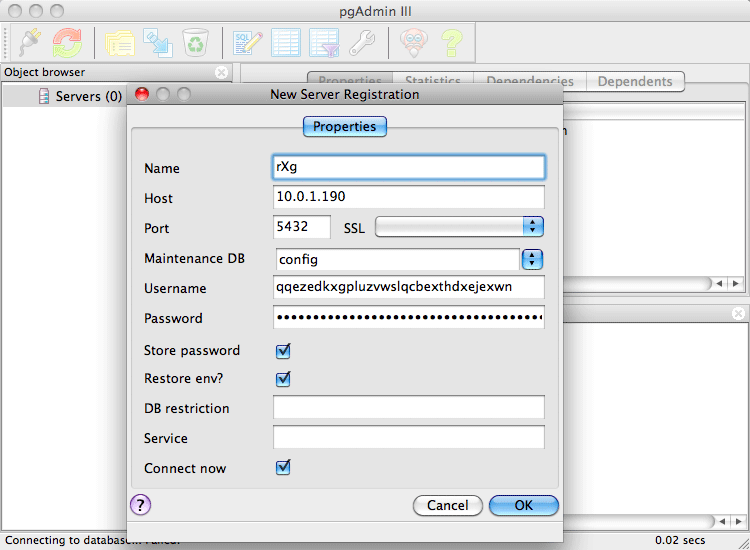
Remote database access is a powerful tool for operators who wish to integrate the rXg with third-party devices, systems and software. Nearly any form of read-only integration may be achieved. To obtain read-write access to the database, the rXg API key mechanism (discussed in the Adminis view) must be used.
Database
Entries in the database scaffold define the remote access policy and credentials for the local database on an rXg. This scaffold is only accessible on an rXg that is configured to use a local server database storage type.
The active field enables an option set. Exactly one option set may be active at any time. Enabling a particular option set will automatically disable another existing active option set.
The name field is an arbitrary string descriptor used only for administrative identification. Choose a name that reflects the purpose of the record. This field has no bearing on the configuration or settings determined by this scaffold.
By default, access to rXg services are either limited to the LAN or disabled entirely. In certain cases, the operator may desire to permit accessibility to services over the WAN and/or LAN. To enable access to rXg services over the WAN, the operator should specify one or more WAN targets containing the list of allowed hosts and then set the visibility appropriately. If no WAN target is specified and WAN visibility is enabled, any node on the WAN may connect to the service. It is highly recommended that this wide-open configuration be avoided to ensure system security. If LAN visibility is included then all authenticated nodes on the LAN may access this service.
The username and password fields contain the credentials for accessing the database. These credentials are generated by the rXg and are immutable.
The note field is a place for the administrator to enter a comment. This field is purely informational and has no bearing on the configuration settings.
NTP Server
The rXg incorporates a sophisticated Network Time Protocol server implementation that serves dual roles within your network infrastructure. Acting both as a time synchronization client to maintain precise local timekeeping and as a time distribution server for downstream network devices, the rXg NTP service ensures consistent temporal accuracy across your entire managed environment. This comprehensive time synchronization capability is fundamental to the reliable operation of billing systems, security protocols, log correlation, and numerous other time-sensitive network services.
Time Synchronization Architecture
The rXg NTP implementation utilizes a hierarchical approach to time distribution, positioning itself strategically between authoritative time sources and client devices throughout your network. The system continuously synchronizes with configured upstream NTP servers while simultaneously providing time services to local area network clients, access points, infrastructure devices, and other network elements that require accurate temporal references.
During periods when upstream connectivity becomes unavailable, the rXg maintains service continuity by automatically transitioning to its internal clock reference configured as a stratum 10 time source. This failover mechanism ensures that network devices can continue receiving time synchronization services even during extended uplink outages, preventing time drift that could compromise security certificates, log file timestamps, and billing accuracy.
Configuration Profile Management
NTP server operation is governed through configuration profiles defined in the NTP Server scaffold, where the active field designates which configuration set controls current system behavior. The rXg enforces a single active configuration policy, automatically deactivating any previously active profile when a new one is enabled. This approach prevents configuration conflicts while enabling administrators to maintain multiple operational profiles suited for different network conditions or maintenance scenarios.
The name field provides administrative identification for each configuration profile, allowing operators to maintain descriptive labels that reflect the intended purpose or deployment context of each configuration set. While this field serves purely administrative functions and does not influence operational behavior, meaningful naming conventions facilitate configuration management in complex environments with multiple operational profiles.
Network Access Control and Security
The rXg NTP server implements comprehensive access control mechanisms that balance service availability with security requirements. By default, NTP services operate with restrictive access policies that limit client interactions while preventing potential security vulnerabilities. The system automatically restricts client capabilities to essential time query functions while blocking administrative operations that could compromise server integrity.
Visibility settings provide granular control over service accessibility across network boundaries. When internal visibility is configured, NTP services become available exclusively to devices connected to local network segments, providing time synchronization for infrastructure equipment, user devices, and access points within the managed environment. The WAN visibility option extends service availability to external networks, enabling remote devices or distributed network components to synchronize with the rXg time source.
WAN targets configuration provides additional security refinement when external access is required. Rather than exposing NTP services to unrestricted internet access, administrators can specify particular host addresses or network ranges that should be permitted to access the time service. This targeted approach maintains security while accommodating legitimate external synchronization requirements for distributed infrastructure or partner network integration scenarios.
Upstream Server Configuration and Authentication
The rXg maintains synchronization accuracy through connection to authoritative time sources configured in the associated Device Option profile. Multiple upstream servers can be specified to ensure redundancy and accuracy, with the system automatically managing server selection and failover based on network reachability and synchronization quality metrics. When no specific servers are configured, the system defaults to the public NTP pool infrastructure, providing reliable time synchronization for standard deployments.
Authentication capabilities enable secure time synchronization in environments where time source verification is critical for security or compliance requirements. The system supports symmetric key authentication using a comprehensive range of cryptographic hash algorithms including MD5, SHA-1, SHA-256, SHA-384, SHA-512, and modern alternatives such as SHA-3 and BLAKE2 variants. Each authentication configuration requires a unique key identifier ranging from 1 to 65535, along with the shared secret key and specified algorithm type.
Authentication key management follows security best practices by requiring unique key identifiers within each device option scope, preventing key collision issues that could compromise synchronization integrity. The system validates authentication parameters during configuration to ensure compatibility with upstream server requirements and cryptographic standards.
Interface Binding and Network Optimization
The rXg NTP implementation includes intelligent interface management designed to optimize performance while avoiding potential socket limitations in complex network environments. Rather than binding to all available network interfaces, which could create resource constraints in networks with extensive VLAN configurations, the system selectively listens on uplink interfaces required for upstream synchronization and localhost for client service delivery.
Client access is facilitated through packet filter redirection mechanisms that transparently route NTP requests to the localhost service endpoint. This architecture enables comprehensive client service coverage while maintaining efficient resource utilization and avoiding the socket limitations that could occur when attempting to bind directly to thousands of VLAN interfaces in large-scale deployments.
The interface selection process automatically adapts to network configuration changes, including uplink modifications, address updates, and interface state transitions. This dynamic adaptation ensures consistent service availability as network infrastructure evolves without requiring manual intervention or service disruption.
Service Reliability and Health Monitoring
Operational reliability is maintained through comprehensive monitoring and automatic service management capabilities integrated into the rXg task execution framework. The NTP service automatically responds to configuration changes affecting network interfaces, addressing, uplink connectivity, and server specifications by regenerating appropriate configuration files and restarting services as necessary to maintain optimal operation.
Health monitoring systems continuously evaluate synchronization status and generate appropriate notifications when time synchronization failures occur or when upstream server connectivity is compromised. These monitoring capabilities integrate with the broader rXg notification infrastructure, enabling administrators to receive timely alerts regarding time service disruptions that could affect dependent systems.
The service management framework includes coordination with other system components to prevent conflicts during maintenance operations and ensure proper startup sequencing during system initialization. Priority scheduling ensures that time synchronization is established before dependent services that require accurate timestamps, such as monitoring data collection and log rotation processes.
Integration with Infrastructure Components
The NTP server seamlessly integrates with other rXg subsystems to provide comprehensive network timing services. Access points and infrastructure devices can be automatically configured to use the rXg as their primary time source, reducing dependency on external time services while improving synchronization accuracy through reduced network hop counts. This integration is particularly valuable in environments where infrastructure devices have limited external connectivity or where centralized time source management is preferred for security or operational reasons.
DHCP and network configuration services can automatically distribute NTP server information to client devices, enabling automatic time synchronization configuration without requiring manual client setup. This automated distribution capability ensures consistent time synchronization across user devices while reducing configuration complexity and support requirements.
The billing system integration ensures that time synchronization accuracy meets the stringent requirements necessary for precise usage tracking, session duration calculations, and financial transaction logging. The system maintains synchronization accuracy standards that support legally compliant billing practices and audit requirements in commercial service provider environments.
The note field is a place for the administrator to enter a comment. This field is purely informational and has no bearing on the configuration settings.
SNMP Server
Entries in the SNMP Server scaffold define configuration profiles for the rXg integrated SNMP server. Many of the instruments that may be accessed via the rXg administrative console are also available via SNMP. This allows the rXg to be probed by a SNMP network or element management system and enables the operator to use to integrate the rXg as part of a large scale heterogeneous network.
The active field enables an option set. Exactly one option set may be active at any time. Enabling a particular option set will automatically disable another existing active option set.
The name field is an arbitrary string descriptor used only for administrative identification. Choose a name that reflects the purpose of the record. This field has no bearing on the configuration or settings determined by this scaffold.
The community is the read only (r/o) string that is used to gain access to this rXg via SNMP. Remote access to SNMP is disabled by default.
The port field specifies which port the SNMP server should listen for SNMP probes.
By default, access to rXg services are either limited to the LAN or disabled entirely. In certain cases, the operator may desire to permit accessibility to services over the WAN and/or LAN. To enable access to rXg services over the WAN, the operator should specify one or more WAN targets containing the list of allowed hosts and then set the visibility appropriately. If no WAN target is specified and WAN visibility is enabled, any node on the WAN may connect to the service. It is highly recommended that this wide-open configuration be avoided to ensure system security. If LAN visibility is included then all authenticated nodes on the LAN may access this service.
The Receive Traps option enables the SNMP Trap listener on the rXg. Access to the server is restricted by the visibility and WAN Target selections. SNMP agents may use the community string specified here or the community string of an Infrastructure Device.
The note field is a place for the administrator to enter a comment. This field is purely informational and has no bearing on the configuration settings.
SNMP MIBs
Integrating any network device with an SNMP monitoring solution usually requires MIBs. The following is list of MIBs that are available to download to assist with SNMP integration to the rXg:
- ADTRAN-VWLAN-MIB.txt
- ADTRAN-VWLAN-PF-MIB.txt
- ADTRANVWLAN-TC.txt
- ADVWLAN-ROOT.txt
- ATM-TC-MIB.txt
- BGP4-MIB.txt
- CISCOSB-BRIDGEMIBOBJECTS-MIB.txt
- CISCOSB-DEVICEPARAMS-MIB.txt
- CISCOSB-MIB.mib.txt
- CISCOSB-TRAPS-MIB.mib.txt
- DIFFSERV-DSCP-TC.mib
- DIFFSERV-MIB.mib
- DVMRP-MIB.txt
- ENTITY-MIB.txt
- IEEE8021-SECY-MIB.mib
- IGMP-MIB.txt
- INTEGRATED-SERVICES-MIB.mib
- IPMROUTE-MIB.txt
- IPV6-MLD-MIB.mib
- LLDP-MIB.txt
- MPLS-TC-STD-MIB.mib
- MSDP-MIB.txt
- P-BRIDGE-MIB.txt
- POWER-ETHERNET-MIB.txt
- Q-BRIDGE-MIB.txt
- RADIUS-DYNAUTH-SERVER-MIB.txt
- RAPID-CITY-MIB.txt
- RMON2-MIB.txt
- RUCKUS-ADAPTER-MIB.txt
- RUCKUS-DEVICE-MIB.txt
- RUCKUS-DHCP-MIB.txt
- RUCKUS-ETH-MIB.txt
- RUCKUS-EVENT-MIB.txt
- RUCKUS-HWINFO-MIB.txt
- RUCKUS-L2TP-MIB.txt
- RUCKUS-PPPOE-MIB.txt
- RUCKUS-PRODUCTS-MIB.txt
- RUCKUS-RADIO-MIB.txt
- RUCKUS-ROOT-MIB.txt
- RUCKUS-SWINFO-MIB.txt
- RUCKUS-SYSTEM-MIB.txt
- RUCKUS-TC-MIB.txt
- RUCKUS-UPGRADE-MIB.txt
- RUCKUS-VF2825-MIB.txt
- RUCKUS-WLAN-MIB.txt
- RUCKUS-WLINK-MIB.txt
- RUCKUS-ZD-AAA-MIB.txt
- RUCKUS-ZD-AP-MIB.txt
- RUCKUS-ZD-EVENT-MIB.txt
- RUCKUS-ZD-SYSTEM-MIB.txt
- RUCKUS-ZD-WLAN-CONFIGURATION-MIB.txt
- RUCKUS-ZD-WLAN-MIB.txt
- SAMSUNG-TELECOM-PRODUCTS-MIB
- SAMSUNG-TELECOM-SMI
- SAMSUNG-TELECOM-TC-MIB
- SAMSUNG-WEC-IF-MIB.my
- SAMSUNG-WEC-IPAPPL-MIB.my
- SAMSUNG-WEC-NW-MIB.my
- SAMSUNG-WEC-SEQ-MIB.my
- SAMSUNG-WEC-SMI
- SAMSUNG-wec8050-MIB.mib
- SAMSUNG-wec8050-TC-MIB.mib
- TOKEN-RING-RMON-MIB.txt
- VRRP-MIB.mib
- WING-MIB.mib
- WS-SMI.mib
The current set of MIB files distributed with the rXg can be downloaded here: MIBs.zip
A number of standard IETF MIBs are also included, namely:
- DISMAN-EVENT-MIB
- HOST-RESOURCES-MIB
- IF-MIB
- IP-FORWARD-MIB
- IP-MIB
- IPV6-ICMP-MIB
- IPV6-MIB
- MTA-MIB
- NET-SNMP-MIB
- NOTIFICATION-LOG-MIB
- RFC1213-MIB
- SNMP-FRAMEWORK-MIB
- SNMP-MPD-MIB
- SNMP-USER-BASED-SM-MIB
- SNMPv2-MIB
- SNMP-VIEW-BASED-ACM-MIB
- TCP-MIB
- UCD-SNMP-MIB
- UDP-MIB
The standard IETF MIB files can be downloaded here: MIBs OS.zip
TFTP Server
Entries in the TFTP Server scaffold define configuration profiles for the rXg integrated TFTP server. May third-party networking devices are configured by loading files over TFTP. The intended use of the rXg integrated TFTP server is to simplify the process of configuring and configuring provisioning of third-party devices.
The TFTP server delivers files out of /space/tftpboot. It is assumed that the operator will use SFTP to transfer files to the rXg that will be served by the rXg integrated TFTP server. In addition, the rXg captive portal may be customized to generate files into this directory for zero operator intervention provisioning scenarios. For example, the captive portal may be customized to generate files for provisioning VoIP ATAs and telephones for end-users who have purchased a usage plan that incorporates a VoIP package.
The active field enables an option set. Exactly one option set may be active at any time. Enabling a particular option set will automatically disable another existing active option set.
The name field is an arbitrary string descriptor used only for administrative identification. Choose a name that reflects the purpose of the record. This field has no bearing on the configuration or settings determined by this scaffold.
The WAN targets and policies fields specify which sets of hosts should be allowed access to the rXg integrated TFTP server. TFTP does not include any authentication. Thus, by default, no access is allowed to the rXg integrated TFTP server. The operator must specifically enable access to hosts on the WAN by creating WAN targets and enabling the appropriate check boxes. Hosts on the LAN may be granted access by placing the hosts into a group and then linking them into a policy which is selected here.
The note field is a place for the administrator to enter a comment. This field is purely informational and has no bearing on the configuration settings.
iPerf Server
Entries in the iPerf Server scaffold define configuration profiles for the rXg integrated iPerf server. iPerf is the de-fato standard mechanism for measuring the available network bandwidth. To use this feature of the rXg, the operator must have an iPerf client installed on one or more external devices.
The active field enables an option set. Exactly one option set may be active at any time. Enabling a particular option set will automatically disable another existing active option set.
The name field is an arbitrary string descriptor used only for administrative identification. Choose a name that reflects the purpose of the record. This field has no bearing on the configuration or settings determined by this scaffold.
The port field configures the port that the iPerf server will be listening for connections on. The default port is 5201.
The WAN targets and policies fields specify which sets of hosts should be allowed access to the rXg integrated iPerf server. iPerf does not include any authentication. Thus, by default, no access is allowed to the rXg integrated iPerf server. The operator must specifically enable access to hosts on the WAN by creating WAN targets and enabling the appropriate check boxes. Hosts on the LAN may be granted access by placing the hosts into a group and then linking them into a policy which is selected here.
The rXg integrated iPerf server is most often used with devices on the LAN to instrument the maximum bandwidth between an end-user device and the rXg. The maximum speed reported by iPerf will be determined by the physical media speed and the bandwidth queue that is associated with the client device. Note that if the end-user has been associated with a usage quota, the use of iPerf will be counted into the quota.
iPerf may also be used from the WAN side to instrument the maximum bandwidth available on WAN uplinks. In order to acquire correct data, the iPerf client should be placed immediately adjacent to the rXg on the WAN. Using a iPerf client that is multiple hops away from the rXg will usually provide nonsensical results because it is impossible to guarantee that the intermediate hops will have sufficient bandwidth for the test.
The use of iPerf is highly preferred to web-based online bandwidth meters such as speedtest.net. This is because the iPerf server enables the operator to independently test the LAN distribution network and the WAN uplinks. A web-based online bandwidth meter can only perform a complete end-to-end test that does not provide any information as to where the potential problem is. Also, the results from an web-based online bandwidth meter test may be skewed by proxies, including the rXg integrated transparent web proxy.
The note field is a place for the administrator to enter a comment. This field is purely informational and has no bearing on the configuration settings.
MQTT Server
Entries in the MQTT Server scaffold define configuration profiles for the rXg integrated MQTT server.
The active field enables an option set. Exactly one option set may be active at any time. Enabling a particular option set will automatically disable another existing active option set.
The name field is an arbitrary string descriptor used only for administrative identification. Choose a name that reflects the purpose of the record. This field has no bearing on the configuration or settings determined by this scaffold.
The WAN targets and policies fields specify which sets of hosts should be allowed access to the rXg integrated MQTT server. MQTT does not include any authentication. Thus, by default, no access is allowed to the rXg integrated MQTT server. The operator must specifically enable access to hosts on the WAN by creating WAN targets and enabling the appropriate check boxes. Hosts on the LAN may be granted access by placing the hosts into a group and then linking them into a policy which is selected here.
The note field is a place for the administrator to enter a comment. This field is purely informational and has no bearing on the configuration settings.
EST Server
Entries in the EST Server scaffold define configuration profiles for the rXg integrated EST (Enrollment over Secure Transport) server. The EST server provides RFC 7030 compliant certificate enrollment services for OpenWiFi access points and other infrastructure devices requiring automated certificate management.
The EST server enables zero-touch certificate provisioning for OpenWiFi deployments, allowing access points to automatically discover and enroll with the rXg certificate authority via DHCP Option 224. This eliminates manual certificate distribution and ensures secure, authenticated communication between access points and the OpenWiFi WSS (WebSocket Server) client.
The active field enables an option set. Exactly one option set may be active at any time. Enabling a particular option set will automatically disable another existing active option set. When no EST server option is active, the EST server is completely disabled and returns HTTP 503 for all EST endpoints.
The name field is an arbitrary string descriptor used only for administrative identification. Choose a name that reflects the purpose of the record. This field has no bearing on the configuration or settings determined by this scaffold.
The WAN targets and policies fields specify which sets of hosts should be allowed access to the rXg integrated EST server. EST server access follows a fail-secure model: when an EST server option is active but has no policies or WAN targets configured, all access is denied with HTTP 403. The operator must specifically enable access to hosts on the WAN by creating WAN targets that encompass the IP ranges where access points are located. Hosts on the LAN may be granted access by placing the hosts into IP groups linked to policies which are then associated with the EST server option.
The EST server uses the same effective policy resolution logic as the rest of the rXg system. When a client requests access, the system determines the client's effective policy using standard group membership rules and checks if that policy is associated with the active EST server option. This ensures consistent access control behavior across all rXg services.
The note field is a place for the administrator to enter a comment. This field is purely informational and has no bearing on the configuration settings.
EST Server Endpoints
The EST server provides standard RFC 7030 endpoints:
/.well-known/est/cacerts- Returns CA certificate chain in PKCS#7 format/.well-known/est/simpleenroll- Handles certificate enrollment requests/.well-known/est/simplereenroll- Handles certificate renewal requests
Integration with OpenWiFi
The EST server integrates seamlessly with OpenWiFi deployments:
- Automatic Discovery: Access points use DHCP Option 224 to discover the rXg hostname for EST services
- Certificate Binding: Certificates include MAC address binding via subjectAltName for device correlation
- Automatic Renewal: Access points automatically renew certificates at 66.6% of validity period with device-specific jitter
- Zero-Touch Provisioning: New access points automatically create inventory records during first enrollment