Payload Rewriting
The payload rewriting feature of the rXg allows operators to dynamically modify the content of any or all HTML pages that transit the rXg. Payload rewriting is embodied by two key features: HTML injection and HTML rewriting. HTML injection enables operators to easily add content to transit web pages. HTML rewriting enables operators to arbitrarily modify the HTML of transit web pages.
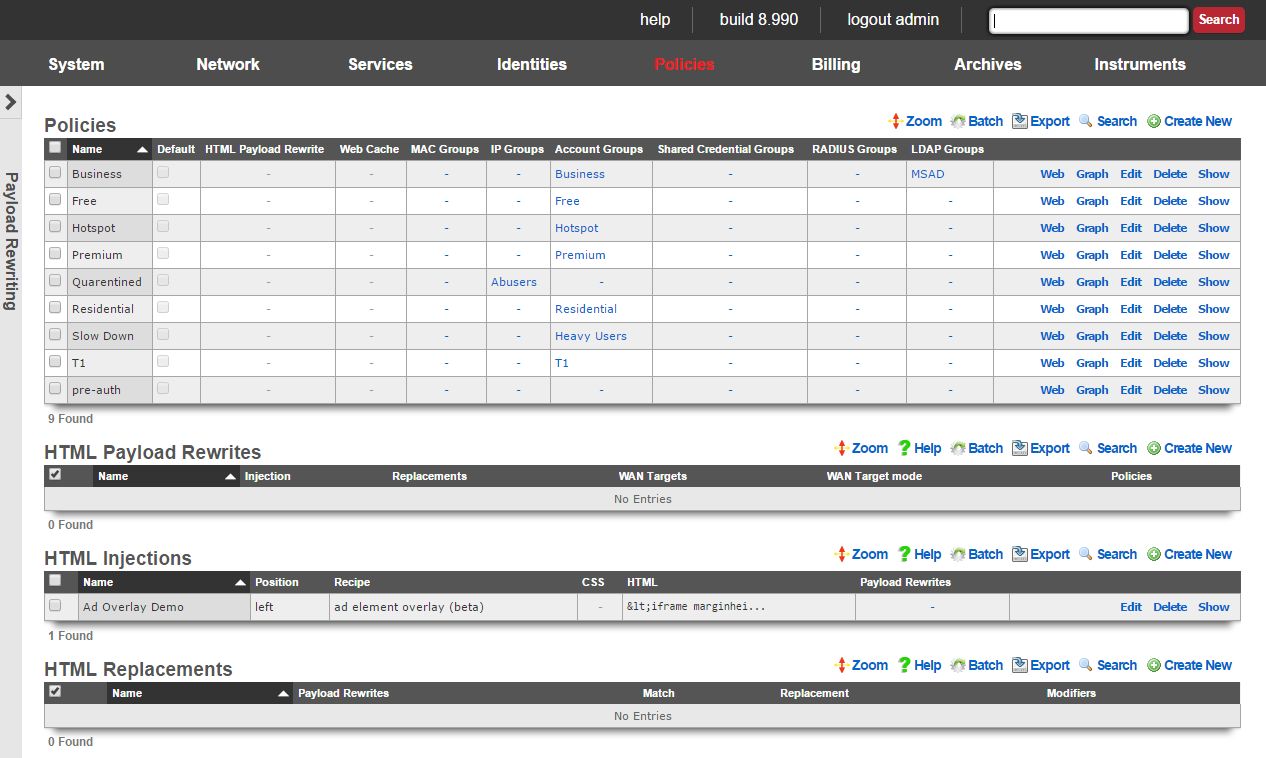
Enabling the payload rewriting feature of the rXg is accomplished by add the desired rewriting configurations into a HTML Payload Rewrites record which is related to a Policy. The effect of the rewrite is controlled by configuring the HTML Injections and HTML Rewrites scaffolds.
HTML Payload Rewrites
The HTML payload rewrites scaffold configures the replacement of web content in web pages that transit the rXg. It is used to link the definitions of desired rewriting configured in the HTML Injections and HTML Rewrites scaffolds to a Policy.
The name field is an arbitrary string descriptor used only for administrative identification. Choose a name that reflects the purpose of the record. This field has no bearing on the configuration or settings determined by this scaffold.
The WAN targets field limits the effect of the HTML payload rewrite settings defined by this record to traffic that is originating from or destined to the IP addresses or DNS names listed in the selected WAN targets. By default, an HTML payload rewrite record affects all HTTP traffic matched by the policy regardless of WAN origin / destination. Setting a WAN target causes the breadth of the HTML payload rewrite to be limited to the specified hosts in the manner specified by the WAN target mode.
The WAN target mode field determines the effect of choosing WAN targets. When set to ignore, all HTTP requests originating from end-users and devices selected by the associated policy will take part in the HTML payload rewrite except for the requests that are headed to the IP addresses and DNS names in the chosen WAN targets.
The policy field relates this record to a set of groups through a policy record.
The note field is a place for the administrator to enter a comment. This field is purely informational and has no bearing on the configuration settings.
HTML Injections
The HTML injections scaffold configures the insertion of operator specified web content into web pages that transit the rXg.
The name field is an arbitrary string descriptor used only for administrative identification. Choose a name that reflects the purpose of the record. This field has no bearing on the configuration or settings determined by this scaffold.
The position field specifies the location where the operator specified web content will be inserted into every web page that transits the rXg.
The recipe field configures which methodology the rXg will use to inject HTML content into web pages. Setting this field to virtual frames will result in HTML content being injected as a header, footer or sidebar (depending on the setting of the position ). Setting this field to floating overlay results in the injected HTML payload being delivered in a stylized HTML div element that floats over existing web content. The ad element overlay option is a specialized recipe designed to work with the rXg integrated advertising rotation mechanism to deliver advertising overlay.
The CSS and HTML fields specify the web content that will be inserted into every web page that transits the rXg.
The policy field relates this record to a set of groups through a policy record.
The note field is a place for the administrator to enter a comment. This field is purely informational and has no bearing on the configuration settings.
HTML injection is a unique capability of the rXg that enables operators to insert snippets of HTML into any transit web page. When enabled, the response from upstream web servers (or local stores if the persistent cache is enabled) are buffered into the RAM of the rXg. The payload is then analyzed for compatibility with injection.
Compatible payloads are rewritten according to the operator selected recipe. The virtual frames recipe converts the original web page into one that uses CSS to emulate frames. The original web content appears at the center of the frame emulated page with operator specified content around the four edges.
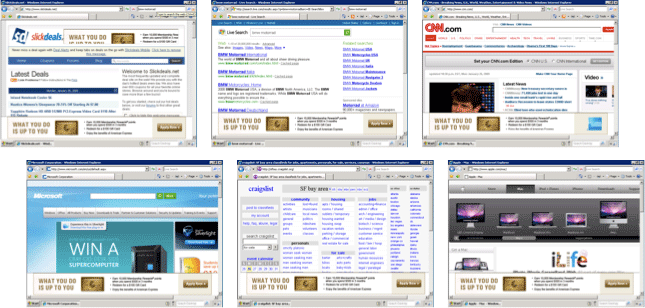
The floating overlay recipe enables operators to insert contant that they desire in a stylized HTML div that is present on all web pages. A small red button is present so that the end-user may close the overlay in case critical content is residing behind the div.
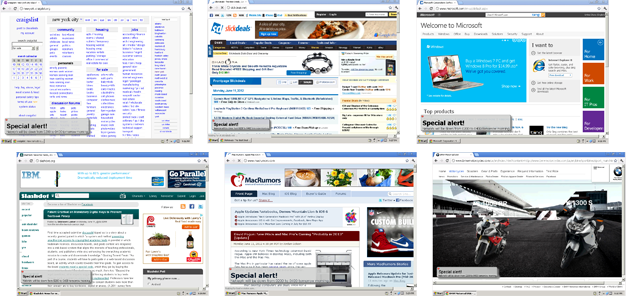
The ad element overlay recipe specifically targets well known advertising delivery mechanisms for HTML injection. This recipe demonstrates the ability of the rXg to seemlessly deliver advertising impressions by overlaying existing publisher-controlled advertisments with operator-controlled advertising inventory.
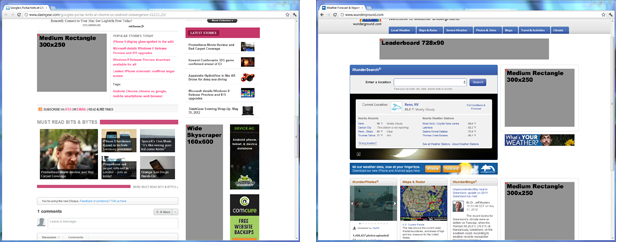
The ad element overlay recipe works in conjunction with the rXg integrated advertising delivery mechanism. This recipe expects that rotators named "160x600," "180x150", "300x250" and "728x90" exist. Rotatees associated with the appropriate rotator should contain the operator-controlled advertising inventory that will be overlaid on top of publisher-controlled advertising content that is present on web pages. Furthermore, the advertising overlay script must be executed by injecting:
<script type='text/javascript'>
adRotatorOverlay();
</script>
HTML injection is typically deployed for three purposes: messaging, up-selling and advertising.
One common application of HTML injection is operators to broadcast messages to the end-user population. Operators are most often going to communicate service messages such as notification of a scheduled system outage. Some operators choose to make use of HTML injection messaging as part of a larger emergency notification system strategy. Sometimes it is possible for operators to leverage this capability to partially fund their networks using federal emergency management grants.
Operators may also use the HTML injection mechanism to up-sell premium services. For example, injection may be used to bring parts of the captive portal into the view to allow an end-user to easily purchase more quota, higher rate limits, etc. In a typical deployment, a quota trigger is configured to place end-users with high percentage or absolute value of quota utilization into a transient group that is associated with a policy that has injection enabled. The injection payload is then configured to notify the end-user of their high utilization and offer them the option of clicking through to purchase more quota and/or upgrade to a higher bandwidth plan.
Many operators choose to use the HTML injection mechanism to deliver advertising. By incorporating operator specified content into potentially every single web page that transits the rXg, a tremendous number of advertising impressions may be generated. In a typical deployment, HTML injection used to generate advertising impressions is associated with a policy that contains "free" end-users while paid end-users do not experience any advertisements.
HTML Replacements
The HTML replacements scaffold configures the generic search-and-replace engine for web pages that transit the rXg.
The name field is an arbitrary string descriptor used only for administrative identification. Choose a name that reflects the purpose of the record. This field has no bearing on the configuration or settings determined by this scaffold.
The match field the string that the engine will use to search for. The entirety of the match field will be replaced with the contents of the replacement field. Parenthesis may be used to store all or part of the contents in the match field for use in the replacement field.
The replacement field is the string that will be used by the engine to replace the match string. The replacement field may contain text or substitution variables such as $1, $2, etc. The number after the $ represents the contents of the parenthesis specified in the match.
The replacement field may also contain a server-side include substitution variable of the form %ssi%FILENAME%. For example, %ssi%/space/portals/your_portal/static/abc.html% will substitute tag with the contents of the file abc.html.
The note field is a place for the administrator to enter a comment. This field is purely informational and has no bearing on the configuration settings.
HTML rewriting enables operators to perform "search and replace" on the web pages that transit the web page. The operator configures a string to match and a string to replace. The rXg loads each transit web page in memory and looks for the match string. If found, the match string is removed and the replacement is inserted in its place.
Consider the following example:
<html>
<head>
<title> A Simple Page</title>
</head>
<body>
<h1> Simple Web Page </h1>
This is the simplest web page possible.
Here is an image:
<img src="/some_photo.jpg"/>
</body>
</html>
If a HTML rewriting record is created with the match field set to simplest and the replacement field set to most complicated, the resulting web page that the end-user sees would be:
<html>
<head>
<title> A Simple Page</title>
</head>
<body>
<h1> Simple Web Page </h1>
This is the simplest web page possible.
Here is an image:
<img src="/some_photo.jpg"/>
</body>
</html>
HTML rewriting records apply to every part of the HTML present in the web page. This allows the operator to effect dramatic changes to the look and feel as well as the structure of the web page. For example, it is possible to create a match rule to replace the stylesheet referenced by a page or add a CSS class to every instance of a particular element. The generic nature of the HTML rewriting engine opens up a broad spectrum of possible applications.