Identities
Identity management is a critical prerequisite to achieving complete control, clear communication and total cognizance over an end-user population. The rXg must understand the who an end-user is before it can determine policy enforcement and properly instrument usage.
The rXg utilizes a two layer approach to identity management. End-users are first individually identified through one of several authentication mechanisms such as credentials passed into the captive portal or operator predefined MAC addresses or IP ranges. Identified end-users are then placed into one or more groups.
Policy enforcement is determined by the policy object that is associated with the group that the individual identity resolves to. Resolution of an identity when multiple group memberships exist determined by the priority field that is present in every group object.
The default rXg captive portal web application supports numerous authentication mechanisms. Operators may choose to authenticate end-users against one or more of the following on board credential stores:
- login user name and password
- single and multiple use tokens
- shared secrets Operators may also choose to use the default captive portal web application to authenticate end-users against external credential stores that support the following protocols:
- RADIUS
- LDAP The operator may also choose to identify end-users without the use of a captive portal. To accomplish this, the operator may specify group membership by one or more of the following:
- Individual MAC address
- Individual IP address
- CIDR range of IP addresses
Identities Dashboard
The identities dashboard presents an overview of the current status and configured settings for the various authentication mechanisms integrated into the rXg.
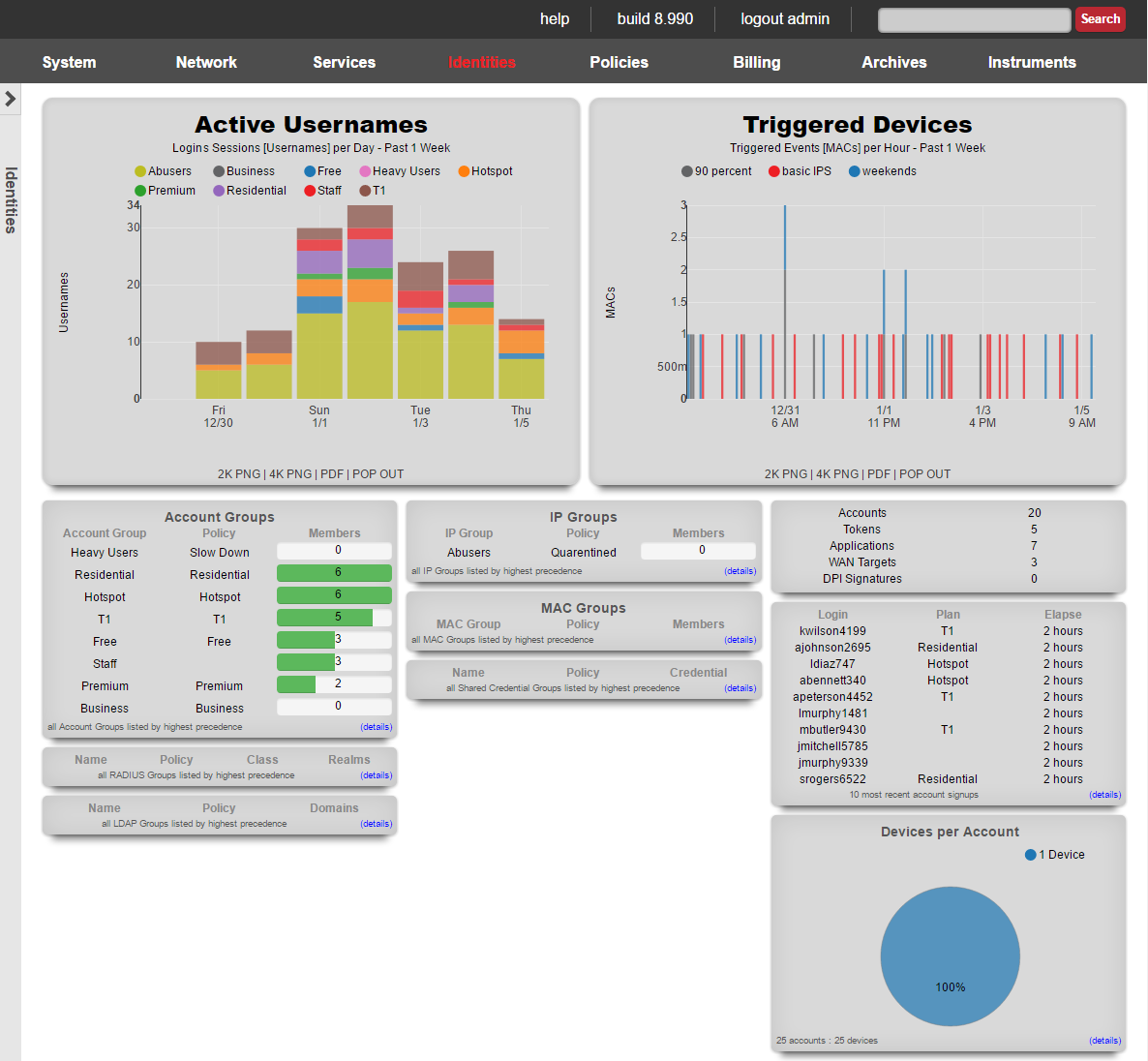
The top dialog in the left column presents a summary of the account groups on the rXg.
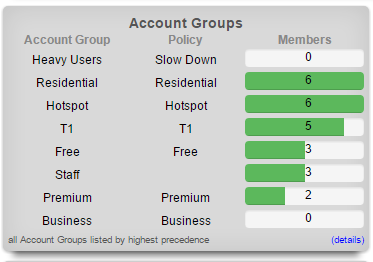
Account groups are listed next to the policy they are enforcing along with the current number of members and the billing plan that sends new end-users into the group.
The center and lower dialogs in the left column present summaries of the rXg external authentication mechanisms.
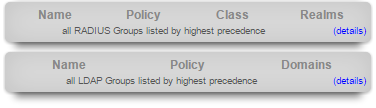
The top dialog displays a summary of the RADIUS NAS client that is integrated into the rXg captive portal web application. Each RADIUS group is displayed along with the policy that will be enforced upon the members of the group. In addition, the RADIUS Class attribute that will determine group membership (if any) and the policy that is enforced upon the members of the group is displayed.
The bottom dialog displays a summary of the LDAP client that is integrated into the rXg captive portal web application. Each LDAP group is displayed along with the policy that is enforced upon members of the group as well as which LDAP domains are queried during a credential challenge.
In the center column, there are three dialogs that present a summary of the currently configured IP groups, MAC groups, and shared credential groups.
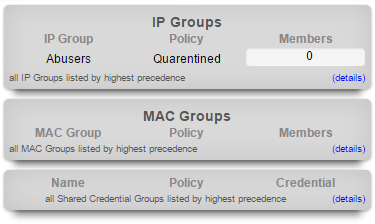
The top dialog presents a list of the IP groups that are currently configured on the rXg. Each IP group is displayed along with the policy that is being enforced upon members of the group. In addition, the number of CIDR blocks assigned to each group is listed at the right. Similar dialogs are found at the bottom of the center column presenting a summary of the MAC and shared credential groups.
The rightmost column presents additional summary dialogs.
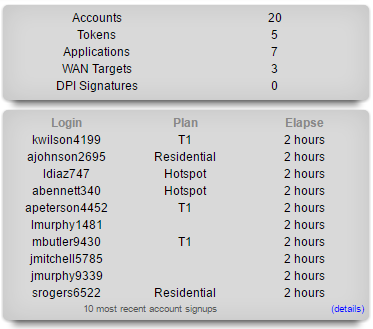
The dialog in the right column presents the 10 most recent end-user signups. Here, the login name, selected usage plan and elapsed time since the signup event are presented.
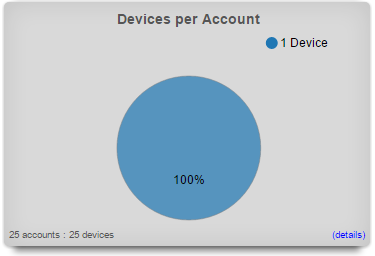
The bottom dialog in the right column presents the average number of devices per account.