Packet Forwards
The packet forwards view presents the scaffolds that configure settings to modify the per-packet forwarding configuration.
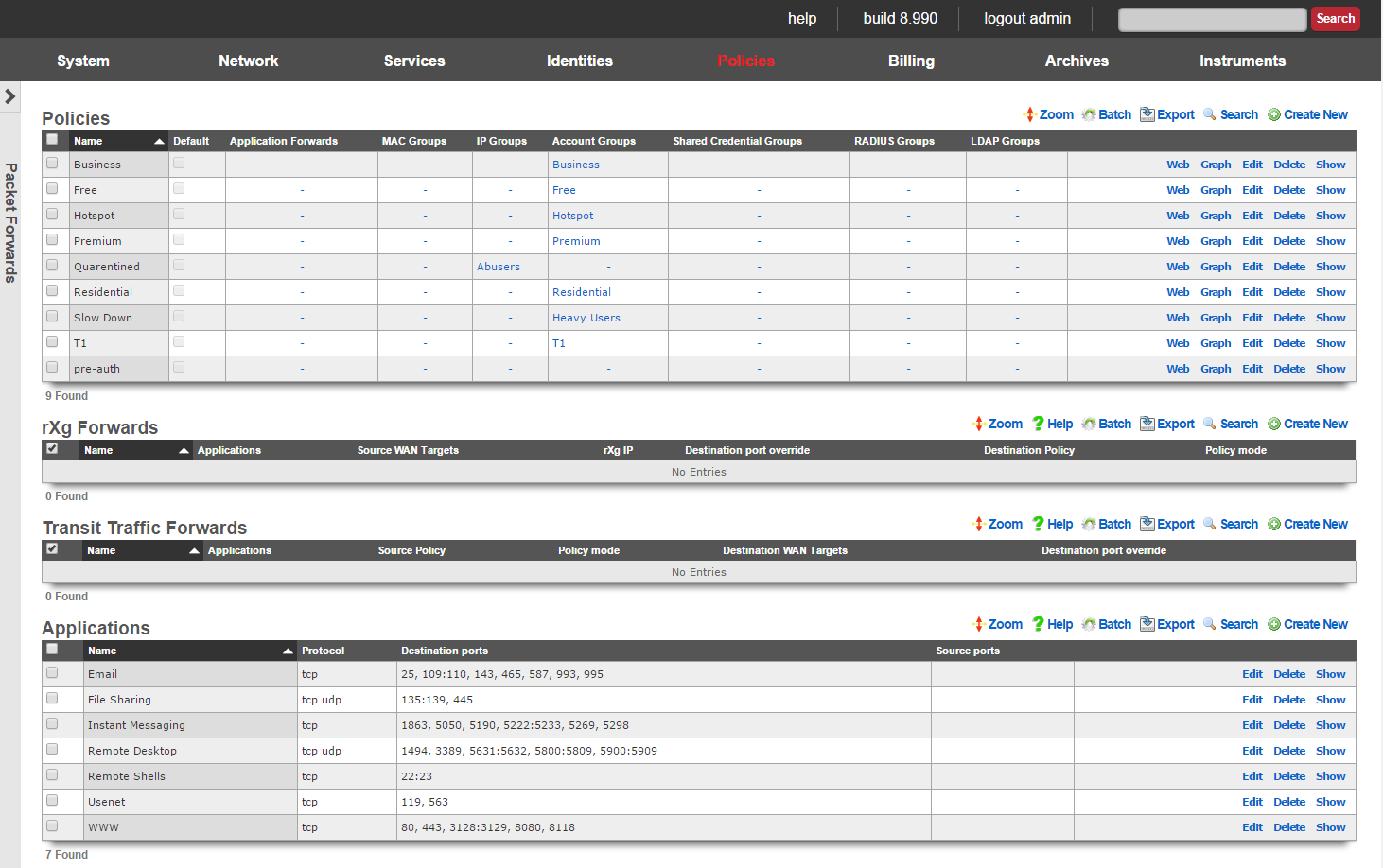
The rXg packet forwarding engine enables the revenue generating network operator to reroute traffic according to predefined rules. There are classes of forwarding rules that the operator may specify. The operator may choose to create rXg forwards that reroute traffic that is originally destined for the rXg. In addition, the operator may choose to create transit traffic forwards that reroute traffic that originates from the LAN and is transitting the rXg ot the WAN.
rXg forwards enable the operator to deploy publicly accessible services on hosts that are on private IP addresses and using NAT to access the WAN. In a typical scenario, rXg forwards are used to enable remote access to infrastructure management mechanisms, public web servers, etc. When deployed generically, this concept is called port forwarding.
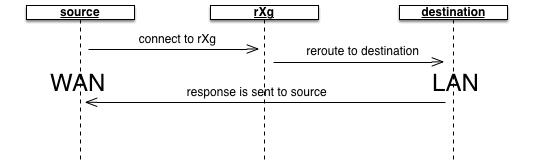
The rXg packet forwarding mechanism builds upon the generic port forwarding concept by enabling the same port to be forwarded to different hosts depending on the originating (WAN) host. In addition, the application forward is limited in effect via policy. This enables the revenue generating network operator to use application forwarding to sell a premium service in a similar manner to application filters.
Transit traffic forwards enable the operator to reroute end-user traffic to operator specified destinations. In a typical scenario, transit traffic forwards are used to require end-users to use operator specified proxies. For example, transit traffic forwards are particularly useful for rerouting all outbound email tranmissions through an operator specified SMTP relay. Another example would be to forward all Jabber IM requests to a Jabber proxy that injects advertising.
The operator specifies which end-users are affected by transit traffic forwards through policies. This fits naturally with the rXg zero operator intervention provisioning methodology and enables operators to deploy transit traffic forwarding as a premium service. For example, hotspot operators may desire to charge a premium for SMTP relay.
rXg Forwards
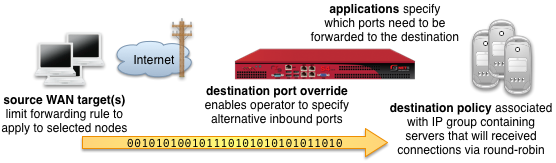
An entry in the rXg forwards scaffold creates a packet forwarding rule that reroutes traffic originally destined for the specified applications on the rXg to a destination specified by one or more IP groups associated with the selected policy.
The name field is an arbitrary string descriptor used only for administrative identification. Choose a name that reflects the purpose of the record. This field has no bearing on the configuration or settings determined by this scaffold.
The applications field configures the class(es) of packets that will be forwarded by the rules generated as a result of this record. Selecting multiple application groups applies this rule to all of the selected applications (logical or).
The source WAN targets field limits the effect of the inbound application forward rule defined by this record to traffic that is originating from the IP addresses or DNS names listed in the selected source WAN targets. By default, an rXg forward rule acts as a generic port forwarder that redirects all traffic matching the configured applications. Setting a source WAN target causes the rXg forward to limit the breadth of the rule to packets originating from the specified host(s).
The destination port override field specifies an alternative port to send the forward traffic. If left unspecified, the original destination port specified by the application is used as the destination port. If specified, all traffic is redirected to the selected port. For example, if the application is configured to be SMTP (destination port 25) and the destination port override is configured to be 587, all port 25 traffic will be forwarded to port 587 on hosts contained in the destination policies.
The policy field relates this record to a set of groups through a policy record.
The policy mode field configures the forwarding behavior when the linked policy contains multiple groups or multiple members in a group. The first member only option causes all traffic coming in from the WAN to the port specified by the application to be forwarded to the first member of the first group. The round-robin option causes inbound traffic on the port specified by application to be load balanced between all members linked to the policy. If only a single group with a single member is linked to the enforcement record, the behavior will be identical to first member only. This option is useful for having inbound requests load balanced to a farm of servers. The autoincrement option causes the enforcement record to create a many to many mapping between ports and group members. For example, if the application specifies a port of 5000, and the policy links to a group with members 10.0.1.100, 10.0.1.101 and 10.0.1.102, then port 5000 will forward to 10.0.1.100, port 5001 will forward to 10.0.1.101, port 5002 will forward to 10.0.1.102, etc. The autoincrement option is useful for easily configuring remote monitoring of a large number of LAN devices when site-to-site VPN is not possible.
The note field is a place for the administrator to enter a comment. This field is purely informational and has no bearing on the configuration settings.
Transit Traffic Forwards
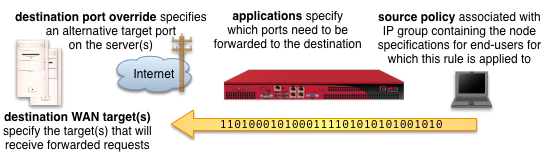
An entry in the transit traffic forwards scaffold creates a forwarding rule that reroutes traffic originating from the LAN to the destination specified on the WAN. The rXg transit traffic forwarding mechanism supports generic (universal) port forwarding as well as policy specific forwarding.
The name field is an arbitrary string descriptor used only for administrative identification. Choose a name that reflects the purpose of the record. This field has no bearing on the configuration or settings determined by this scaffold.
The applications field configures the class(es) of packets that will be forwarded by firewall rules generated as a result of this record. Selecting multiple application groups applies this rule to all of the selected applications (logical or).
The policy field relates this record to a set of groups through a policy record.
The policy mode field for outbound forwards is always set to round-robin. If only a single WAN target is specified, then all traffic will always be redirect to the specified WAN target. If multiple WAN targets are specified, outbound traffic is load balanced amongst the specified WAN targets /.
The destination WAN targets field specifies the destination of the traffic for the transit traffic forward. If multiple hosts are defined by the specified WAN targets, the destinations are forwarded connections on a round-robin basis.
The destination port override field specifies an alternative port to send the forward traffic. If left unspecified, the original destination port specified by the application is used as the destination port. If specified, all traffic is redirected to the selected port. For example, if the application is configured to be SMTP (destination port 25) and the destination port override is configured to be 587, all port 25 traffic will be forwarded to port 587 on hosts contained in the destination WAN targets.
The note field is a place for the administrator to enter a comment. This field is purely informational and has no bearing on the configuration settings.