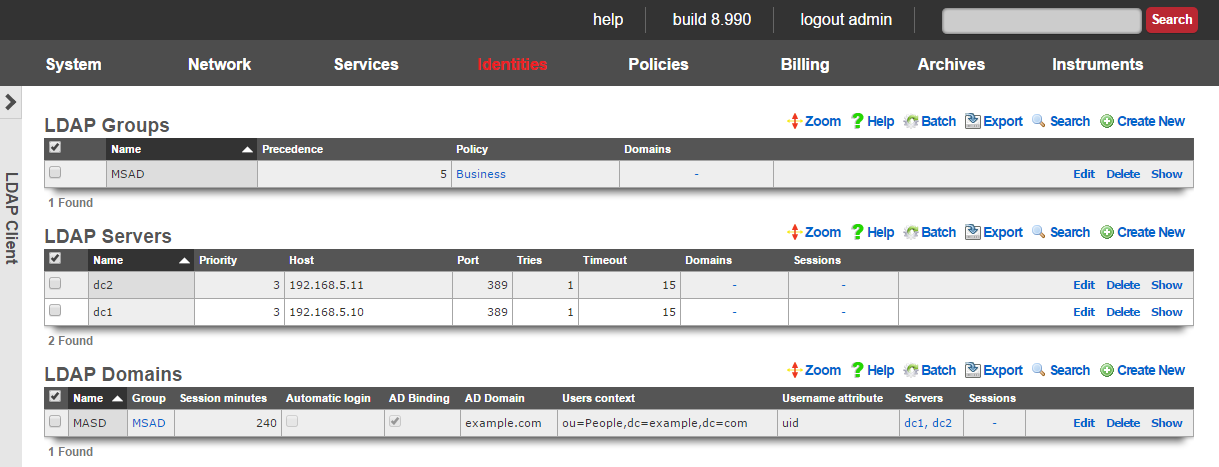
LDAP Client
The LDAP client view presents the scaffolds associated with manipulating the external LDAP server identity management integration mechanisms built into the rXg captive portal web application.
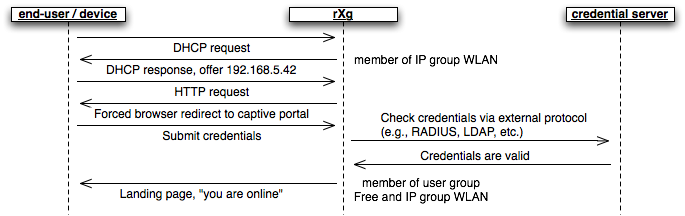
When an external LDAP server is used as the credential store, the captive portal must be enabled. The end-user web browser is then redirected to the rXg captive portal web application. At this point, the end-user must present credentials to the external authentication client that is integrated into the portal. The end-user supplied credentials are then sent to an external LDAP server. The response is then interpreted by the rXg integrated external authentication client and access to the WAN is manipulated appropriately.
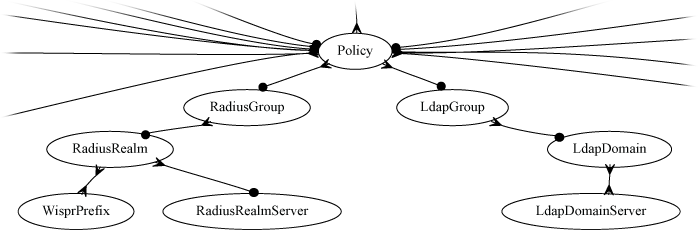
Group membership is determined by the creation of the LDAP groups records and the association of those records with LDAP domains. In addition, LDAP groups are associated with policies in a manner similar to local groups ( MAC groups , IP groups and account groups ).
Several LDAP domain records may be configured to support multiple simultaneous logical partitions. For example, an operator may choose to have separate LDAP domain records for students and faculty in a campus setting as those two sets of identities may be either stored on different LDAP servers or as cousins in a large LDAP hierarchy of a single server.
Access to LDAP servers is defined by the associated records in the LDAP servers scaffold. Following the above example, if students and faculty are stored as cousins within the same LDAP hierarchy, two LDAP domains would be associated with a single LDAP server. Of course, if the two end-user pools are stored in different trees, then distinct LDAP server records must be created for the server hosting each tree. Multiple LDAP server records may be associated with a single LDAP domain to enable server failover.
The rXg LDAP client is fully compatible with Microsoft Active Directory (MSAD). To integrate with an MSAD, the LDAP domain must be designated as such via the AD binding field and the associated LDAP server records must point to MSAD domain controllers. Using both standard LDAP and MSAD servers in the same LDAP domain is not supported.
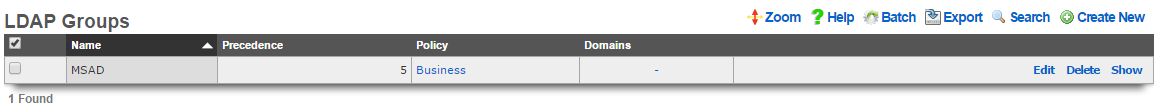
LDAP Groups
The name field is an arbitrary string descriptor used only for administrative identification. Choose a name that reflects the purpose of the record. This field has no bearing on the configuration or settings determined by this scaffold.
An entry in the LDAP groups scaffold defines a group object that can be used as a membership destination for end-users that have been authenticated via the LDAP protocol.
The priority field determines the effective group when an end-user or device is a member of more than one group. By default, LDAP groups have a priority of 4, which puts them ahead of the default priority of all group objects configured by internal identities.
The LDAP domains field determines which logical partitions of the LDAP client will send end-users to become members of this LDAP group (and hence, take part in the enforcement defined by the policy ).
The policy field associates this group object with a policy object. The policy object relates the group to objects that specify the configuration of the control and communication features of the rXg that determine the end-user experience.
The note field is a place for the administrator to enter a comment. This field is purely informational and has no bearing on the configuration settings.
LDAP Servers
An entry in the LDAP servers scaffold defines a server that may be queried for end-user credential validation using the LDAP protocol.
The name field is an arbitrary string descriptor used only for administrative identification. Choose a name that reflects the purpose of the record. This field has no bearing on the configuration or settings determined by this scaffold.
The priority field is used when multiple LDAP servers are associated with a LDAP domain. The LDAP server with the highest priority is queried first.
The IP field specifies the IP address of the LDAP server to be queried for credential validation.
The port field specifies the TCP port to use when sending the LDAP query for credential validation. Leave this field blank to use the default.
The tries and timeout fields govern the retry and failure detection behavior of the LDAP client. Increase these values when communicating with servers that are heavily loaded or connected via congested networks.
The LDAP domains field determines which logical partitions of the LDAP client will use the server specified in this record for queries. LDAP trees are designed to support several different organizations and organizational units through a unified hierarchical structure. The same LDAP server may be associated with several different LDAP domains to provide access to different facets of the hierarchy.
The note field is a place for the administrator to enter a comment. This field is purely informational and has no bearing on the configuration settings.
LDAP Domains
An entry in the LDAP domains scaffold defines a logical partition for the LDAP client that is integrated into a captive portal web application.
The name field is an arbitrary string descriptor used only for administrative identification. Choose a name that reflects the purpose of the record. This field has no bearing on the configuration or settings determined by this scaffold.
If the Create Account box is checked, the rXg will create or update an Account object after successful user authentication against the LDAP server. Creating an Account for the user enables the user to take advantage of the manage devices, usage reporting, and DMZ and port forwarding functionality. This behavior is mutually exclusive to specifying an LDAP Group and session attributes.
Associating one or more Usage Plans to the LDAP Domain instructs the rXg to perform a search against the LDAP server to determine group membership. The names of the user's groups are compared against names of the associated Usage Plans to attempt to find a matching plan. If there is a singular match, the Usage Plan is applied automatically. If there are no matches or multiple matches, the Account will be created with no usage plan and the user must select or purchase a usage plan via the captive portal before gaining access to the Internet.
The LDAP group field specifies the membership destination for end-users that have presented valid credentials.
The session minutes field specifies the length of the login session for end-users that have presented valid credentials.
If the automatic login box is checked, the rXg will attempt to automatically login a returning end-user after the first successful authentication, assuming the user has the same MAC address and/or browser cookie. This requires storing the end-user's password in the rXg's database in encrypted format.
If the logical partition of the LDAP client defined by this record is to be used with Microsoft Active Directory, check the box next to AD binding and enter the MSAD domain into the AD domain field.
The Users context field specifies the base DN to be used when searching for LDAP users or when building a user's DN for authentication against a non-Active Directory LDAP server. User records must reside below the specified DN in order to be located via LDAP searches for usage plan matching when Account creation behavior is enabled.
The Username field specifies the LDAP attribute that will be used to build a user's DN when using non-AD binding, as well as for performing searches against LDAP when account creation behavior is enabled. The value should be the name of an attribute identifies the the user's username, such as samaccountname when utilizing Active Directory.
The Bind username and Bind password fields specify the credentials that will be used to perform searches against the LDAP database when Account creation behavior is enabled.
The note field is a place for the administrator to enter a comment. This field is purely informational and has no bearing on the configuration settings.